Authentication is any process by which you verify that someone is who they claim they are. This usually involves a username and a password, but can include any other method of demonstrating identity, such as a smart card, retina scan, voice recognition, or fingerprints.
In security terminology, a biometric security system is an authentication technique that relies on a computer system to electronically validate a measurable biological characteristic which is physically unique and cannot be duplicated. Biometrics security systems are gaining importance because of the increase in the accuracy and reliability of identification and authentication functions. Biometric is the most secure and convenient authentication tool. It can not be borrowed, stolen, or forgotten and forging one is practically impossible. Biometrics measure individual's unique physical or behavioral characteristics to recognize or authenticate their identity.

Various types of biometric security systems are being used for real-time identification; the most popular are based on face recognition and fingerprint matching, iris and retinal scan, speech, facial thermograms, and hand or palm geometry. Behavioral characters characteristics include 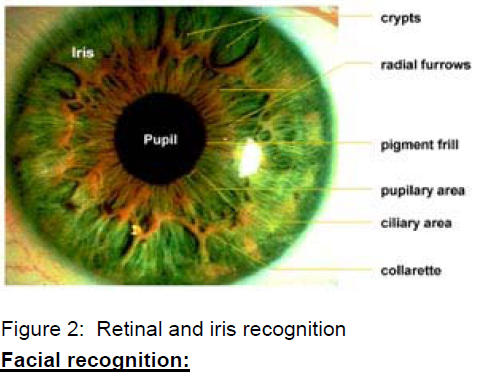
Facial recognition is one of the newer biometric technologies, with systems only recently showing the accuracy necessary for commercial application. Facial recognition records the spatial geometry of distinguishing features of the face.
Facial recognition:
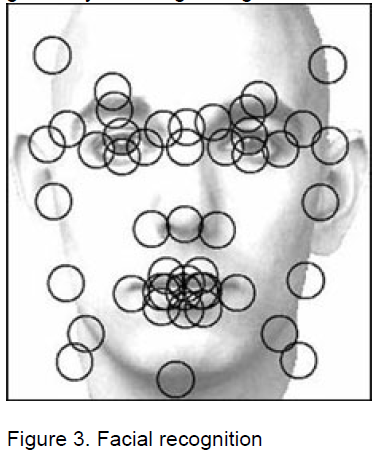
It compares the dimensions of different facial attributes like eyes, nose, ears, etc., and their positions in relation to each other. However, in dim or varying light conditions, the result may not be very accurate. Last year also saw the launch of world’s first face recognition technology for mobile phones.
Five steps to facial recognition are 1. Capture image
2. Find face in image
3. Extract features
4. Compare templates
5. Declare matches
relative pen speeds and pressures has significantly improved the accuracy.

Voice Recognition:
Voice Recognition is a technology which allows a user to use his/her voice as an input device. Voice recognition may be used to dictate text into the computer or to give commands to the computer (such as opening application programs, pulling down menus, or saving work).
Older voice recognition applications required each word to be separated by a distinct space. This allowed the machine to determine where one word begins and the next stops. These kinds of voice recognition applications are still used to navigate the computer's system, and operate applications such as web browsers or spread sheets.
Newer voice recognition applications allow a user to dictate text fluently into the computer. These new applications can recognize speech at up to 160 words per minute.

Hand geometry:
collection (background noise when using a voice biometric).
There are some other vital ingredients to be analyzed:
1. Cost - biometrics devices and their related things, such as installation, connection, user system integration, research and test of the biometric system, system maintenance, etc.
2. User acceptance - certain user groups reject biometric technologies on various grounds because of privacy concerns. Some application-specific requirements like security level, which can be low, moderate or high. This decision will greatly impact which
|
|
signature, voice, keystroke pattern, and gait. Of this class of biometrics, technologies for signature and voice are the most developed.
Retinal scans and iris scans:
Retinal scans are based on the presence of the fine network of capillaries supplying the retina with oxygen and nutrients. These vessels absorb light and can be easily visualized with proper illumination. Retinal scans require close contact of user and scanner, a perfect alignment of the eye with a scanner, and no movement of the eye. The examiner is required to keep the subject's eye within half an inch of the instrument. The subject must focus on a pinpoint of little green light (to properly align the eye) and avoid blinking. A low-intensity coherent light is then transmitted through the eye and the reflected image of the retinal capillary pattern is recorded by the computer.
Retinal scans are considered to be too intrusive for a general security use and the prolonged exposure to light emitted by the scanners might be harmful to the eye. As a result a strong competition to the retinal scans was launched by iris scanning technology.
The colored part of the eye appears to be as unique as fingerprints and retina.
There is only a chance of one in 1078 that two irises will be identical. 
Unlike other biometric systems, facial recognition can be used for general surveillance, usually in combination with public video cameras. Finger Print:
Fingerprint recognition is one of the oldest biometric technologies and its application in criminal identification, using the human eye, has been in use for well over 100 years.
Now a days computer software and hardware can perform the identification significantly more accurately and rapidly. Finger scanning has several methods such as optical, ultrasound and silicon sensors, which work in different ways.
The technology is one of the most developed of all biometric technologies as also the most affordable, due to which it is beginning to make inroads into the mass market.

Signature Recognition:
Electronic Signature Recognition is another biometric technology that has been worked on for some years and the dynamic recognition of Hand geometry involves the measurement and analysis of the shape of one's hand. It is a fairly simple procedure and is surprisingly accurate. Though it requires special hardware to use, it can be easily integrated into other devices or systems. Unlike fingerprints, the human hand isn't unique.
Individual hand features are not descriptive enough for identification. However, it is possible to devise a method by combining various individual features and measurements of fingers and hands for verification purposes.

Selecting a Biometric Technology:
1. Ease of use - some biometric devices are difficult to handle unless there is proper training.
2. Accuracy - Vendors often use two different methods to rate biometric accuracy: false-acceptance rate (FAR) or false-rejection rate (FRR). Both methods focus on the system's ability to allow limited entry to authorized users. However, these measures can vary significantly depending on how one adjusts the sensitivity of the mechanism that matches the biometric. There may be instances where FAR decreases and FRR increases. Thus we have to be careful to understand how the biometrics vendors arrive at quoted values of FAR and FRR. Because FAR and FRR are interdependent, we can draw a plot, which can facilitate to determine the crossover error rate (CER). The lower the CER, the more accurate the system
3. Error incidence - Time and environmental conditions may affect the accuracy of biometric data. For instance, biometrics may change as an individual becomes old. Environmental conditions may either alter the biometric directly (if a finger is cut and scarred) or interfere with the data biometric is most appropriate for this kind of applications.
Finally organizations should consider a biometrics’ stability including maturity of the technology, degree of standardization, level of vendor and governmental support, market share and other support factors. Mature and standardized biometric technologies usually have stronger stability.
About the Author: Jyothi Raju Kanike is B. E. Electronics from Hyderabad University, Hyderabad, India. She can be reached at: Jyothi_nngs@yahoo.com |